- AV Industry
- ByHaivision
- Posted
- Products
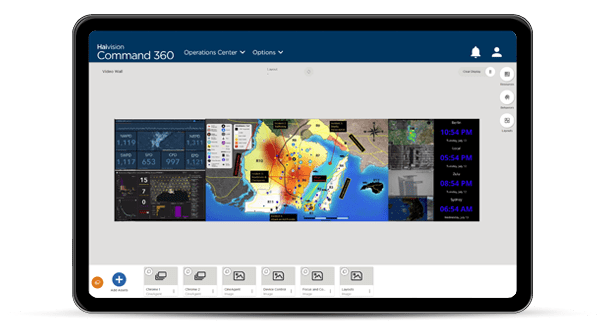
Introducing Haivision Command 360 Platform – the most powerful video wall software for situational awareness and real-time decision-making for mission-critical environments around the world. You’ll gain unmatched, centralized control of your operations with access to more features, streamlined workflows, and the most advanced user interface for tailoring the system to meet your unique requirements. Get started right away without custom programming or extensive training.
- Markets
- Services
- About
- Resources